Identity & Access Management (IAM) forms the core of cybersecurity policies and platforms. Verifying users and securing credentials assist in preventing an overwhelming majority of data breaches. In modern enterprise's digital ecosystem, IAM robust authentication protocol can keep digital assets secure apart from providing a protection shield from external sources. Let us understand what IAM is all about and where is it useful in an enterprise.
What is Identity & Access Management?
Identity & Access Management is a framework used to implement an extra layer of security for enterprise web applications, APIs, enterprise user life cycle management and enterprise applications access provisioning to external users/vendors. IAM can control the user or role based access to enterprise applications and enable single sign in for seamless user authentication with enterprise applications integrated with IAM. It verifies the user access requests and can either grant or deny permission to protected web & app resources enterprise wide.
It allows to administrate the IAM activities such as creating users, groups, defining access roles, policies, protect web application resources and configure authentication schemes from centralised IAM console. There are several advantages of IAM in terms of security enhancements and in automation of business workflow logics resulting in increased work productivity and reduction in the IT staff's workload when it comes to onboarding and deboarding the employees/contractor to access the enterprise applications in large organisations.
Be it healthcare, finance or other sectors, businesses uses IAM in order to comply with best practices and industry standards. In simple terms, it is automating user life cycle for enterprise applications and enables trust with other external entities such as cloud solutions and third party applications. The below picture outlines the IAM user identity life cycle.
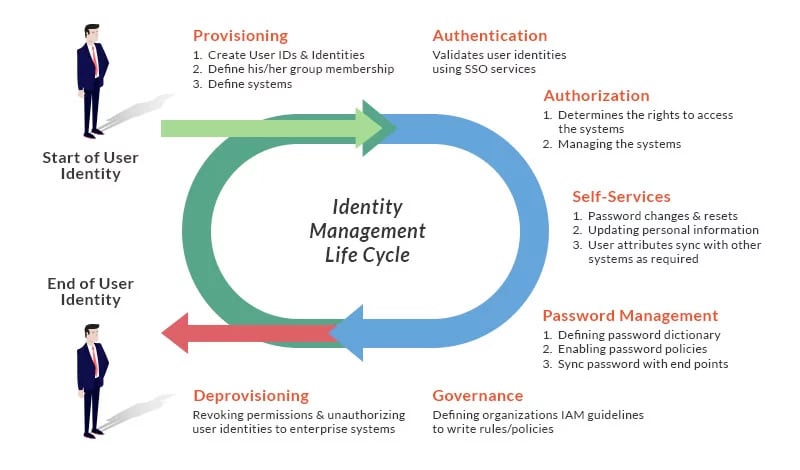
Flow Diagram of Identity and Access Management Sequence
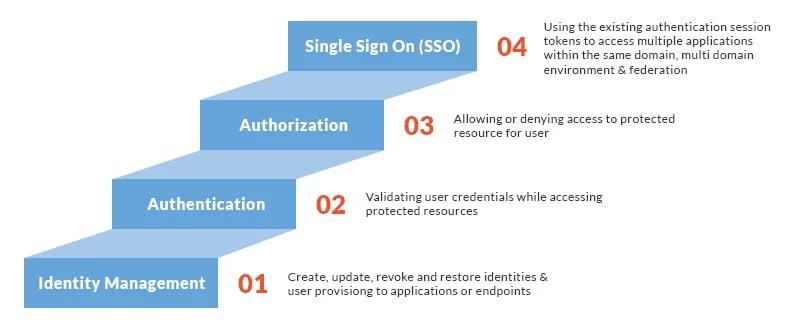
Logical View of IAM Workflow
IAM Architecture
In the below image, we can see the flow of internal and external users accessing the applications hosted in web tier of an organisation. Internal/external users are challenged to provide credentials for authentication using SSO authentication page.
Here, user authentication mechanism can be configured using Forms, X509 Certificate based MFA, Oauth, and SAML 2.0. Post authentication, SSO services will validate the users for application authorisation and redirect them to corresponding application target pages based on their attributes definitions and provisioning roles.
IAM administrator is responsible for framing user profiles/policies/workflows and protect web application resource using SSO component and define the provisioning roles.
For example, let us say, finance department, in an organisation has a provisioning role defined as “finance managers provisioning role” in IAM . On assigning the “finance managers provisioning role,” a user will gain access to all the applications associated with that provisioning role. Similarly, when the same user is de-provisioned from the “finance managers provisioning role,” the same user will loose access to those applications.
Here, we are using common user store for both SSO services and Identity Manager. This user store is used to manage user identities from Identity Manager component.
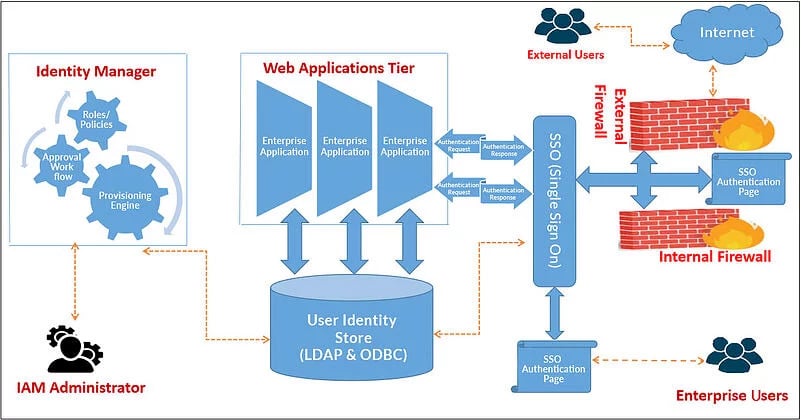
Architectural Flow of IAM
IAM Open Source Tools & Features
Let us go through the commonly used open source IAM tools available and the features supported by these tools.
|
Open Source Tools→ Features ↓ |
OpenIAM |
Central Authentication Services (CAS) |
Keycloak |
WSO2 |
Aerobase |
|---|---|---|---|---|---|
|
SSO |
√ |
√ |
√ |
√ |
√ |
|
Password Services |
√ |
√ |
√ |
√ |
√ |
|
SAML 2.0 Support |
√ |
√ |
√ |
√ |
√ |
|
OAuth 2.0 Support |
√ |
√ |
√ |
√ |
√ |
|
OpenID Protocol |
√ |
√ |
√ |
√ |
√ |
|
Acts as IDP & SP |
√ |
√ |
√ |
√ |
√ |
|
Multifactor Authentication |
X |
√ |
√ |
√ |
√ |
|
Social Logins |
√ |
√ |
√ |
√ |
√ |
|
Identity Life Cycle Management |
√ |
X |
√ |
√ |
√ |
|
Mobile OTP |
√ |
X |
√ |
√ |
√ |
|
Client Certificate |
X |
X |
√ |
√ |
√ |
|
Single Logout |
√ |
√ |
√ |
√ |
√ |
|
Cloud Integration Support |
√ |
√ |
√ |
√ |
√ |
Why Chose Open Source IAM?
- Flexibility: No need to negotiate with vendors for customisation as it is free to explore and pick as required.
- Independent: Since we have complete source code available, no vendor lock-in is required. Moreover, we don’t need to rely on anyone for product support as we can fix the issues ourselves.
- Cost Efficiency: No product licensing is required with low initial cost to do POCs & maintenance cost along with zero upgrade cost using open source.
- Migration/Upgrade: Migration from one IAM tool to other using open source IAM tools is relatively easy because the data stores are not propitiatory.
Challenges in Using Open Source IAM Tools
- Dependency: We have to rely on communities and consortium for troubleshooting issues during implementation as we don’t have concrete documentation at one source for single go.
- Competency: IAM team has to upskill or keep the in-house talent to support open source IAM tools.
- Support: We have to rely on the suggestions that are available in the blogs as getting to the workable source is a difficult task.
- Security Concern: Open source tools are vulnerable because many people contribute in development of the tools and we are unsure of the risks involved.
- Risk Assessment: Deep vulnerabilities assessment and scanning is required while planning to implement it in production. This incurs additional cost and time.
Parameters for Choosing Open Source IAM Tool
The following parameters should be considered while choosing an open source IAM tool:
- Enhancements/Customisation: It should have the capability to extend and customise things as needed.
- Implementation Friendly: In heterogeneous technology stack, integration is easy.
- Scalability: Integration with new application and ability to incorporate new security protocols as and when it emerges.
- Open Standard: Should support open standard protocols.
- Compliance: Should be compliant with cyber security and industry regulations.
Conclusion
Agility in technology trends and adoption of new technology stack is making industries to think before they invest in getting licences for proprietary IAM solutions. Many Fortune 500 companies have implemented and moved towards open source IAM solutions but most of the large enterprises are still using the proprietary IAM products. It may be beneficial for medium and small organisations as an option.
However, there are risks in selecting an open source IAM, which is community-supported and the entry of barriers are greatly reduced apart from funds being allocated towards consulting and providing support to deploy the open source IAM solutions.
Additionally, these core functionalities are at par compared to proprietary IAM products. The sources for documentation are limited, but with open source, it’s easy to download the software and check how it fits into the needs with minimal efforts. If one can get positive outcomes, which can reduce the expenditures, the same funds can be redirected to meet other security enhancements.
About Innominds
Innominds is a leading Digital Transformation and Product Engineering company headquartered in San Jose, CA. It offers co-creation services to enterprises for building solutions utilising digital technologies focused on Devices, Apps, and Analytics. Innominds builds better outcomes securely for its clients through reliable advanced technologies like IoT, Blockchain, Big Data, Artificial Intelligence, DevOps and Enterprise Mobility among others. From idea to commercialisation, we strive to build convergent solutions that help our clients grow their business and realise their market vision.
To know more about our offerings, please write to marketing@innominds.com