Introduction to Artificial Intelligence
One of the most buzzing word of the 21st century is Artificial Intelligence (AI).
There is an obvious confusion when it comes to terms such as AI, Machine Learning (ML) and Deep Learning (DL).
Artificial Intelligence is the process of mimicking a human brain in understanding, thinking, deciding and working to solve a problem. It is the capability of a machine to imitate human behavior.
Machine Learning is the subset of AI. It doesn’t deal with the explicit programming but is the core of AI where the main functionality is to recognize the pattern and use it for predictions. This phenomenon mainly focuses on using and developing algorithm in finding the patterns. Some of the algorithms developed for this are Support Vector Machines (SVM), K-Means, and Naïve Bayes methods, etc.
Deep Learning helps in resolving the challenges like Feature Extraction. The ability to learn and focus on right feature data by the guidance of programmer is the USP of Deep Learning. The ability is achieved by learning from the experience. Deep Learning is a subset of Machine Learning.
- Goal of AI: Giving a machine the ability to think, decision making, etc.
- Goal of ML: Giving a machine the ability to learn from patterns and predictions
- Goal of DL: Giving machines the ability to learn by various approaches quickly

Methods of AI in Information Security
Information Security is all about protecting data from unauthorized access. Required level of security is defined depending upon organization, projects they handle, data they process, etc.
A lot of security practitioners are being lured into believing that AI approaches are the magic silver bullet we have been waiting for to solve all our security challenges. Artificial Intelligence will be leveraged significantly to help with advances in security around two dimensions - accurate identification of flaws (reducing false-positive rate) and pro-active or immediate detection of threats.
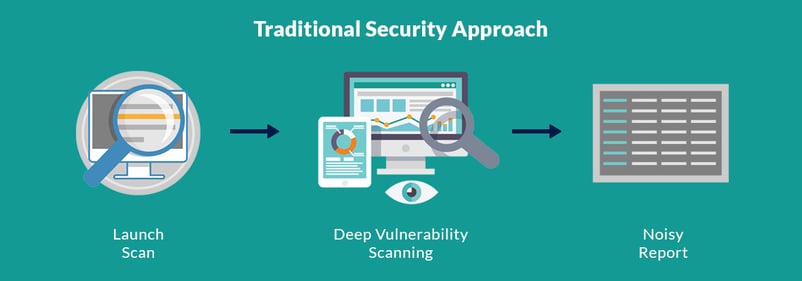
The traditional security tools are predefined with set of plugins, signature patterns and follow standard procedures in assessing the security of the application irrespective of the functionality and behavior of the applications and reports false positives in large amount. Security analysts are spending most of their time in eliminating false positives from the noisy report generated by the automated tools. It takes some time for the security experts to identify potential threats and to perform in-depth security assessment. But Deep Learning or any other Machine Learning is the approach, which has to be incorporated with the security expert’s knowledge for the algorithms to reveal actual security insights.
In information security, we first need to look at our goals. To make it brief, we try to use Machine Learning to identify malicious inputs and application’s behavior.
Within Machine Learning, there are three approaches that are categorized and they are Supervised, Unsupervised and Reinforcement models.
Supervised Learning: The area where the Machine Learning has made the biggest impact in information security is Supervised Learning. Supervised Machine Learning focuses on classifying data (labelled data). These labelled samples are collected from existing common vulnerabilities and vulnerable applications allowing us to train the algorithm to analyze the responses from the report generated by automated tools. AI integrated automated tools eliminates the false positives by analyzing the findings with the training data set. This approach has greatly benefited in accurate identification of flaws from Deep Learning where it has helped drop false positive rates to a very manageable number. This process gives time for the security analyst to evaluate the security loopholes at multiple levels by performing in-depth security assessment and other kinds of social engineering attacks.
Examples
IBM AppScan, Wallarm and Pentoma Immuni-Web are few of the AI driven automated tools, which work efficiently to pinpoint the flaws in applications.
IBM AppScan is an automated penetration testing tool integrated with Artificial Intelligence. This tool performs in-depth scanning and generates the report of potential vulnerabilities with lot of noise and redundancy.
But instead of providing the noisy report directly, it is being analyzed by the Intelligent Finding Analysis (IFA) and provides refined report to the security analyst.
IFA is trained with existing common vulnerabilities from different applications using supervised Machine Learning model. IFA analyze the findings in the below two cycles.
Cycle 1 – It uses pre-defined signatures and filters to set findings as not interesting (false-positive).
Cycle 2 – By using supervised learning and training data set, IFA analyze the responses and payloads used on each finding and determine the findings as Vulnerable, likely Vulnerable and not Vulnerable.
IFA also provides clear description for all the findings that are being included and excluded in the final report dashboard.
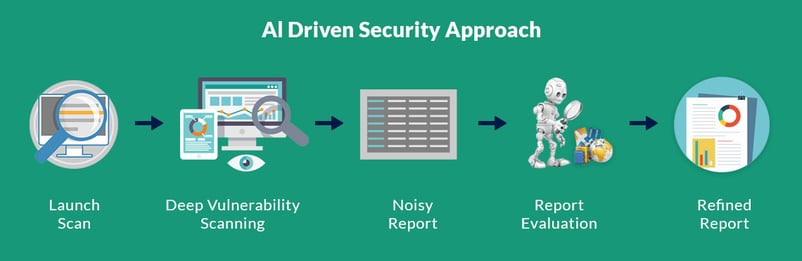
Still, AI can only predict the flaw (It cannot confirm) as human intervention is required to eliminate the false positives and to train the algorithm more efficiently with refined result data sets along with new attack patterns (update trained data set and re-start the server on every update so that the algorithm learns from the updated trained data set).
Unsupervised Learning: Unsupervised approaches are great for data exploration and it uses unlabeled data. They can be used to interpret large amount of data by grouping the records together and extracting features using clustering and association rules. These algorithms help in cyber level to detect the malwares and zero-day attacks as AI has the capability to inspect the data and extract features at deep level.
Examples: SPLUNK and IBM Qradar
These tools are integrated with semi-supervised ML models (provided with labeled and large amount of unlabeled data) and interprets all incoming data at infrastructure level to identify malicious actions and generates alerts. These alerts are analyzed by security analysts to determine whether the alert is actionable or not.
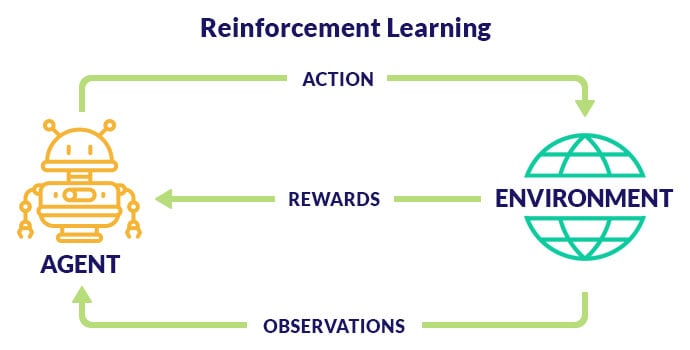
Reinforcement Learning uses AI agent to take actions and improvise from each hacking attempt based on the feedback given by the environment.
Example:
Deep Exploit and Deep-Pwning are few of the Artificial Intelligence driven tools, which work efficiently to identify security flaws at the infrastructure level.
These tools are integrated with Metasploit framework and uses reinforcement learning model to perform intelligence gathering, threat modeling, vulnerability analysis, exploitation and reporting.
 Limitations
Limitations
As Artificial Intelligence learns from experience, security experts are required to ensure that the algorithm is learnt only in a defined and ethical way. Security experts need to train the algorithm with novel attack patterns to work more efficiently.
All automated and intelligent tools are not efficient enough to perform social engineering attacks, authorization checks, business logic checks, etc., which needs to be performed manually to ensure security at multiple levels.
Conclusion
Artificial Intelligence can detect many security flaws and escalate the issue to the attention of security analysts. AI can not only save significant amounts of time of security analysts, but also identify the vulnerabilities, which are not easily identified by any manual techniques. However, it cannot completely replace dedicated security professionals.
Due to the emergence of new attacks, we always need the security analysts to analyze the report generated by the tool and eliminate false positives and train the machine accordingly. So, AI alone cannot resolve the problems in information security. The machines need the inputs from security analysts to get expertise and to learn from the analysis generated by them. A complete secure system can be obtained only when the expertise from security professionals and Machine Learning approachable tools work together.
Author Bio: With more than 15 years of experience in Information Security across APAC and North America, Venkat leads our Enterprise Security business unit and is responsible for custom solutions and service delivery. He works closely with our Enterprise and ISV clients including start-ups and helps achieve their Enterprise Security objectives. You can reach out at vgottipati@innominds.com for any advisory and consultative thought leadership on the topic of Enterprise Security.
About Innominds
Innominds is a leading Digital Transformation and Product Engineering company headquartered in San Jose, CA. It offers co-creation services to enterprises for building solutions utilizing digital technologies focused on Devices, Apps, and Analytics. Innominds builds better outcomes securely for its clients through reliable advanced technologies like IoT, Blockchain, Big Data, Artificial Intelligence, DevOps and Enterprise Mobility among others. From idea to commercialization, we strive to build convergent solutions that help our clients grow their business and realize their market vision.
Interested! For any demos or project discussions, please write to us at marketing@innominds.com and know more about our offerings